Modelo Sip Seguro para una Comunicación extremo a extremo sobre IPV6
DOI:
https://doi.org/10.33017/RevECIPeru2011.0024/Keywords:
sip, tls ,ipv6, srtp.Abstract
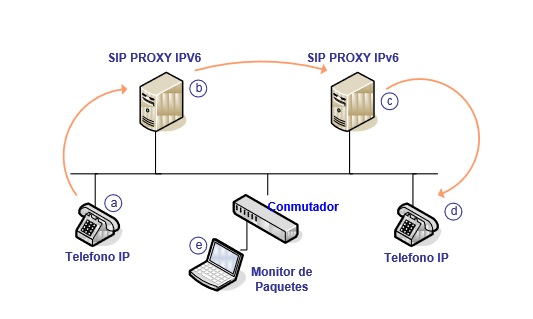
VoIP deployments today have increased considerably, but not all the scenarios consider appropriate security mechanisms. This last point is very important to consider today, especially the depletion of IPv4 addresses and the deployment of many services IPv6, where will new security threats to try to overshadow the great technology boom VoIP. Although IPv6 was developed to solve many security vulnerabilities are currently present in IPv4, the fact is that still fails to achieve these goals by testing. The SIP protocol, the main actor of VoIP technology requires the implementation of security mechanisms. The current scenarios require high-end user performance and support to adapt to heterogeneous security mechanisms or assume trust relationships. But keep in mind that there are various combinations of security solutions that are provided by end users and servers. This paper presents a security model applied to an experimental scenario VoIP over Next Generation Internet (IPv6), which uses hop by hop security and end to end. The proposed scenario is on a local network with IPv6 addresses. Use two Asterisk servers implemented under the same characteristics that act as SIP Proxy, and are connected via SIP trunk - TLS. They also use two user terminals (IP phones) from a known trade mark registered by each SIP-TLS protocol for each server Asterisk. In previous work, there have been several studies on the performance of VoIP using IPv6 and IPv4 and comparing the results [1], evaluation of security mechanisms to support user authentication, confidentiality and integrity of the signaling and media messages VoIP over IPv4 networks [2] and [3]. This paper outlines a framework of security, which presents a scenario based on a VoIP network in IPv6 using TLS and SRTP. TLS is used for the security session establishment authentication mechanisms hop by hop and SRTP (Secure Real Time Protocol) for the safety of the establishment of media stream. We will focus on analyzing and evaluating the security of the messages in this scenario the secure transport protocol (TLS) .